Wordfence and WPScan Publish Mid-Year WordPress Security Report
WPScan is on track to post a record-breaking year for WordPress plugin vulnerabilities submitted to its database, according to a collaborative mid-year security report the company published with Wordfence. In the first half of 2021, WPScan has recorded 602 new vulnerabilities, quickly surpassing the 514 reported during all of 2020.
The report is based on attack data from Wordfence’s platform and data from WPScan’s vulnerability database, providing a more comprehensive picture of the current state of WordPress security than either company could present alone.
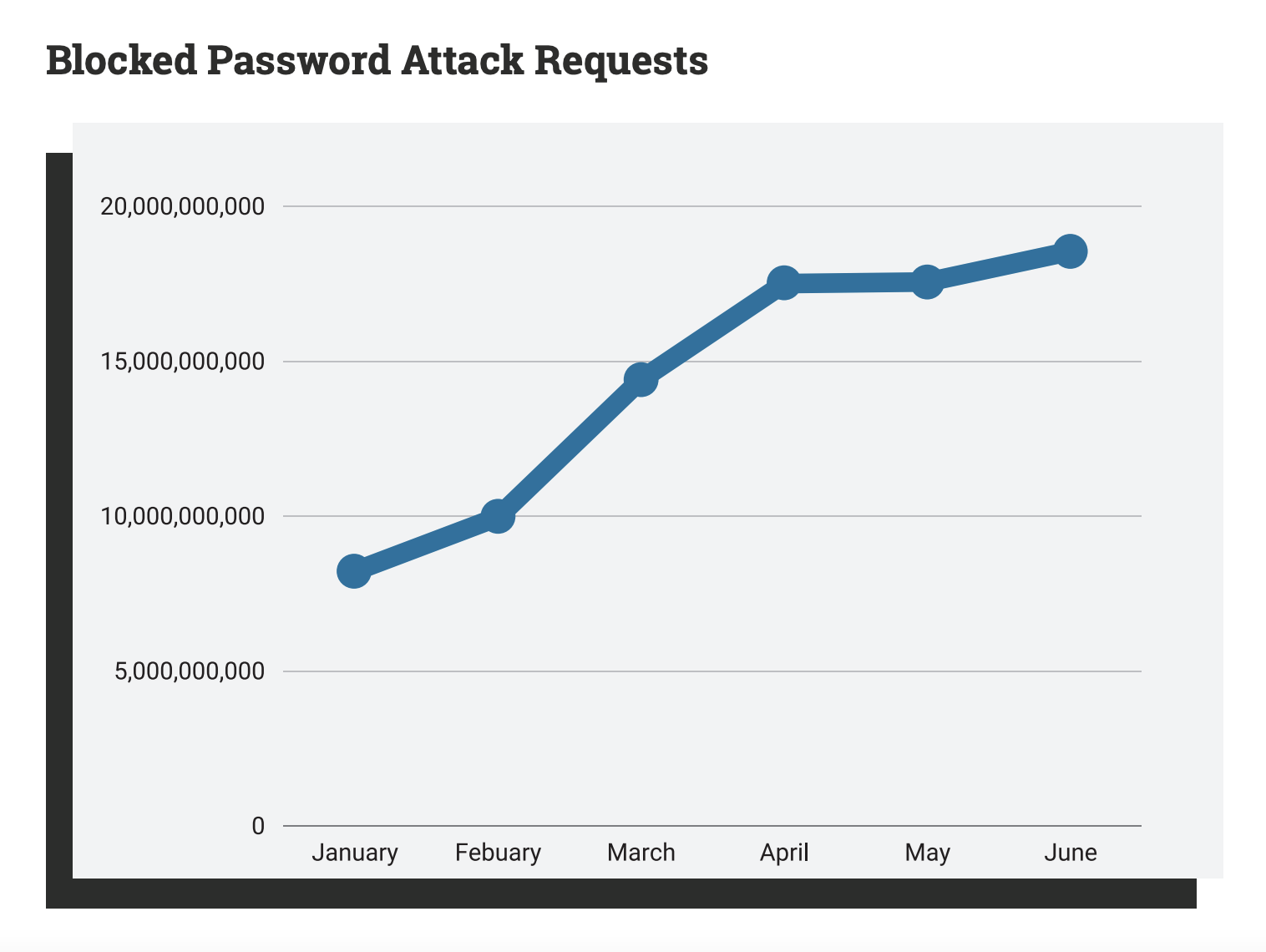
One of the trends highlighted in the report is the increase in password attacks. Wordfence blocked more than 86 billion password attack attempts in the first half of 2021. Attackers use a variety of methods to gain access to WordPress sites, including testing sites against lists of compromised passwords, dictionary attacks, and more resource intensive brute force attacks.
Wordfence found the standard login to be the primary password attack target for 40.4% of attempts, followed by XML-RPC (37.7%). Since these attacks seem to be increasing, the report recommends that site owners use 2-factor authentication on all available accounts, use strong secure passwords unique to each account, disable XML-RPC when not in use, and put brute force protection in place.
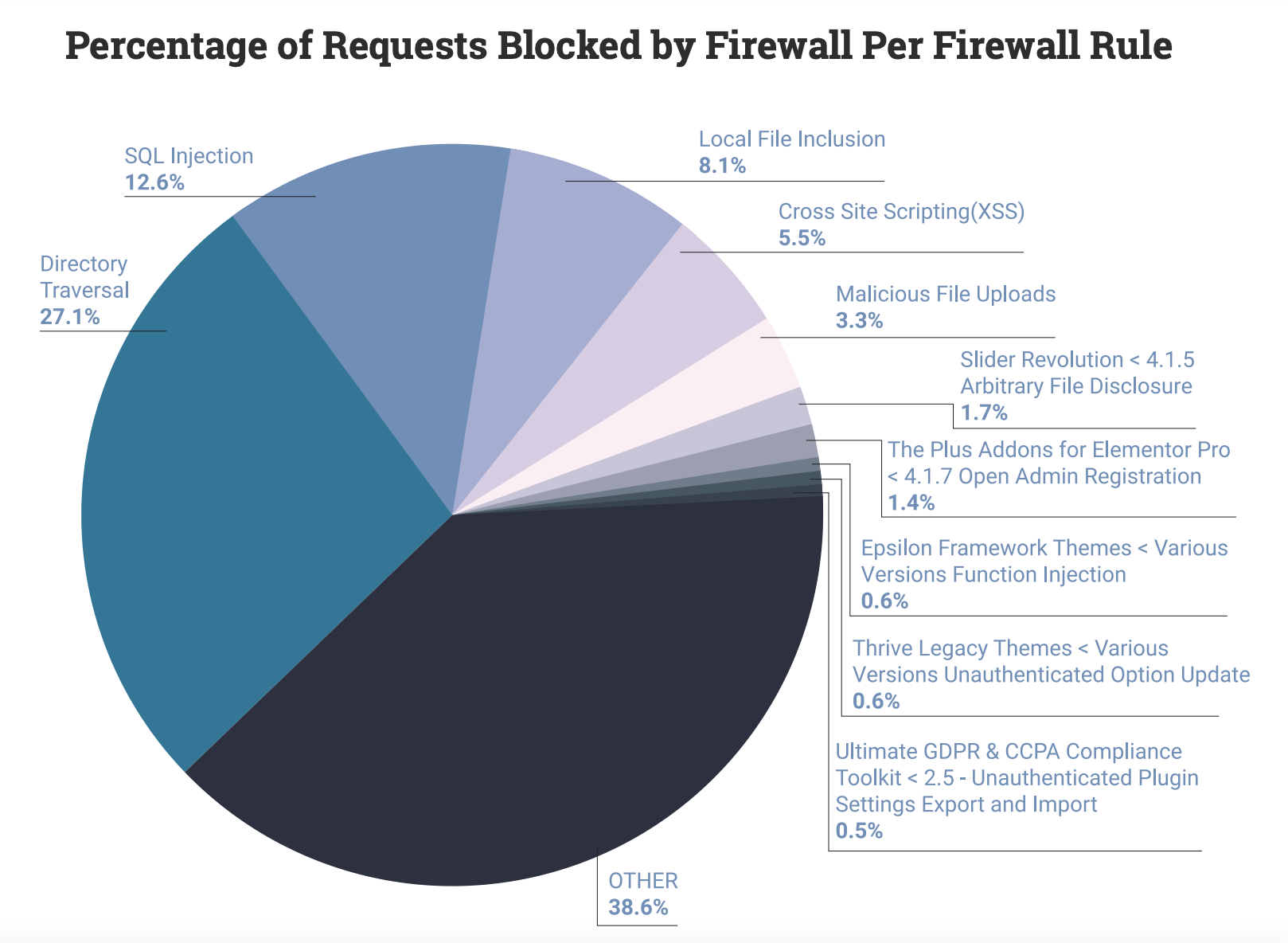
Data from Wordfence’s Web Application Firewall shows more than 4 billion blocked requests due to vulnerability exploits and blocked IP addresses. The report includes a breakdown of the percentage of requests blocked by firewall per firewall rule. Directory Traversal accounts for 27.1% of requests. This is when an attacker attempts to access files without being authorized and perform an action such as reading or deleting a site’s /wp-config.php file, for example. This breakdown also highlights the fact that certain older vulnerabilities are still frequently targeted by attackers.
The vast majority of the vulnerabilities you hear about in the WordPress ecosystem come from plugins, with themes making up a much smaller portion. The report notes that only three of the 602 vulnerabilities catalogued by WPScan in the first half of this year were found within WordPress core.
In analyzing vulnerabilities by type, WPScan found that Cross-Site Scripting (XSS) vulnerabilities accounted for more than half of all them (52%), followed by Cross-Site Request Forgery (CSRF) at 16%, SQL Injection (13%), Access Control issues (12%), and File Upload issues (7%). Using scores from the Common Vulnerability Scoring System (CVSS), WPScan found that 17% of reported vulnerabilities were critical, 31% high, and 50% medium in severity.
Both Wordfence and WPScan claim that the greater number of vulnerabilities reported this year is indicative of the growth of the WordPress ecosystem and a maturing, healthy interest in security. Themes and plugins aren’t getting more insecure over time but rather there are more people interested in discovering and reporting vulnerabilities.
“First and foremost, we aren’t seeing a lot of newly introduced vulnerabilities in plugins and themes but rather we are seeing a lot of older vulnerabilities in older plugins and themes being reported/fixed that just weren’t detected until now,” Wordfence Threat Analyst Chloe Chamberland said.
“Vulnerabilities aren’t being introduced as frequently and more vulnerabilities are being detected simply due to the higher activity of researchers which is in turn positively impacting the security of the WordPress ecosystem. Considering it isn’t newly introduced vulnerabilities that are being frequently discovered, I feel confident in saying that the increase in discoveries doesn’t indicate that the ecosystem is getting less secure at all but rather getting more secure.”
Chamberland also said she believes there is a domino effect when vulnerabilities are disclosed to vendors and they learn from their accidents, causing them to develop more secure products in the future.
“Speaking from experience as I spend a lot of my time looking for vulnerabilities in WordPress plugins, things have definitely been getting more secure from my perspective,” she said. “Today, I frequently find capability checks and nonce checks in all the right places along with proper file upload validation measures in place, and all the good stuff. It’s become harder to find easily exploitable vulnerabilities in plugins and themes that are being actively maintained which is a great thing!”
The mid-year report is available as a PDF to download for free from the WPScan website. WPScan founder and CEO Ryan Dewhurst said he expects there will be an end of the year report for 2021. He has not yet discussed it with Wordfence but the companies are brainstorming about other ways they can collaborate.