Commentary on Sandwich Attacks and MEV, Threats to Decentralized Trading Markets and Countermeasures

victim of sandwich attack
When you used a decentralized exchange (DEX) such as Uniswap to purchase tokens, you had the experience of placing a high-priced buy order due to the difference in touch and trading at a high price. Isn’t there? This phenomenon may be the result of a “sandwich attack”, a fraudulent transaction practice.
A “sandwich attack” is a combination of front-run and back-run, where you unfairly profit from watching other users’ orders, inserting your own large buy orders, and then placing sell orders. is.
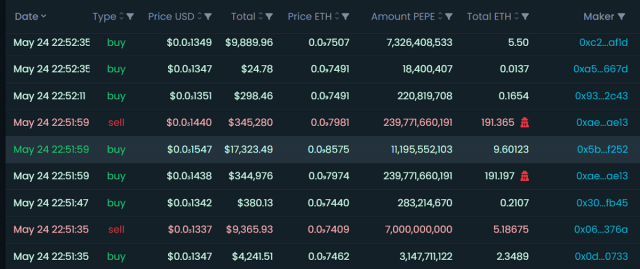
Source: DEXTools
In order to understand specific cases of “sandwich attacks”, refer to the information on the data analysis site “DEXTools”. The site provides visualizations of the transactions associated with the sandwich attack, allowing us to better understand the attack mechanics.
For example, if you look at the trading history of the ‘PEPE’ token on Uniswap, you can see that the central buy order is sandwiched between two trades (marked in red).
Looking at the numbers, the first transaction used 191.197 ETH to buy 239,771,660,191 PEPE, resulting in a transaction price of $0.0s1547 for the victim, about 10% higher than the previous rate. And shortly after that, the same amount of PEPE was sold and the price returned to its previous level again.
As a result, the attackers recovered 191.365 ETH and earned the difference of 0.17 ETH. This is what a sandwich attack looks like.
Such fraudulent activities occur frequently not only on Ethereum (ETH), but also on blockchains with high user and transaction volumes, such as the BNB chain. We users are unaware of its existence and may lose assets in the process of making transactions.
However, there are ways to protect yourself from sandwich attacks by finely setting the allowable range of slippage (price fluctuations) during trading and using DEXs that take measures against front running.
This article focuses on the problem of sandwich attacks in decentralized finance (DeFi) markets on blockchains. We also introduce the general risks associated with this, as well as the larger phenomenon that encompasses these issues: MEV (Maximum Extractable Value).
table of contents
- victim of sandwich attack
- Rise of the Jared bot
- Sandwich attack modus operandi
- Effects of a sandwich attack
- Sandwich attack countermeasures ①: DEX
- Sandwich attack countermeasures ②: MEV Blocker
- MEV Blocker profit return scheme
- Discussion of MEV Burn
Rise of the Jared bot
Recently, the activity of the high-speed trading bot “jaredfromsubway.eth”, which conducts sandwich attacks on decentralized exchanges (DEX), has caused a stir.
The Jared bot routinely performs sandwich attacks to fraudulently withdraw funds from millions of users.
In the midst of the memecoin memecoin boom in April 2011, the Jared bot used front-running, mainly through trading on the emerging memecoin PEPE Memecoin (PEPE), and made huge profits.
According to research by EigenPhi, a decentralized financial data analytics platform, the Jared bot made as much as ¥360 million (approximately $2.7 million) in profits through sandwich attacks in the week starting April 17, 2023.
In addition, it is reported that in the short period from February 27, 2023 to May 8, 2023, when the Jared bot started operation, the total profit earned was about 840 million yen (about $ 6.3 million). .
But how does the Jared bot manage its sandwich attacks? Let’s take a closer look at how it works in detail.
Sandwich attack modus operandi
Sandwich attacks are characterized by clever use of a blockchain function that accumulates unconfirmed transactions called “mempool”.
Imagine yourself as an attacker operating a trading bot. The following transaction A is waiting in mempool.
A: An order to buy a total of 100 ETH at a rate of $2,000 per ETH
With this as a target, attackers will front-run. To do so, it issues its own transaction B, paying a higher gas rate.
B: Order to buy at $2,000 per ETH for a total of 1000 ETH + expensive gas fee
The price of ETH jumps to $2,100 per ETH as Transaction B, which paid the higher gas price, gets prioritized into the blockchain (i.e., the transaction goes through). As a result of this price change, the amount of ETH that can be obtained by A’s order will decrease from 100 ETH to 95 ETH.
Then, after a backrun selling 1000 ETH, the attacker can profit from the difference.
This chain of events is the main sequence of steps in a sandwich attack. Especially when such attacks are carried out on tokens with low liquidity, the price volatility can be as high as 10%, 20% or more. Therefore, the impact of this attack cannot be said to be negligible for general cryptocurrency users.
Effects of a sandwich attack
To maximize the opportunity for sandwich attacks, the aforementioned Jared bot has been found to hold a large amount and variety of tokens compared to other competing bots. The Jared bot held over 800 different tokens at its peak.
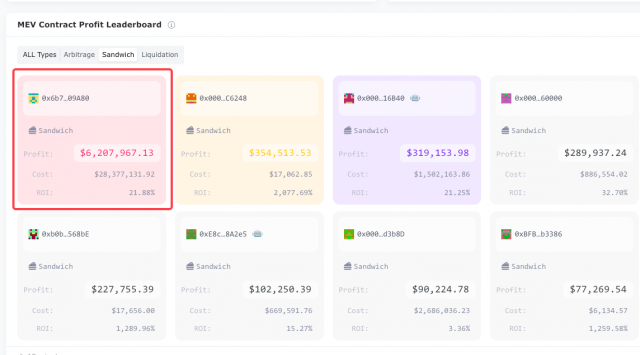
Source: Eigenphi
PEPE Memecoin (PEPE), the meme coin introduced earlier, has increased in value by more than 21,000% in just three days since its launch on April 12, 2011. After that, PEPE reached the 57th place in the cryptocurrency ranking with a market capitalization of about 100 billion yen ($800 million) as of May 10.
Taking advantage of this sharp price increase, the Jared bot launched a series of sandwich attacks. The Jared bot performed similar operations on other memecoins such as Chad Coin (CHAD), NEET, WOJAK, and APED.
During a period of skyrocketing memecoin trading opportunities, the Jared bot consistently inserted front-run deals that paid high gas prices for purchase transactions on the network.
According to EigenPhi’s research, from February 27 to May 8, 2023, Jared bot paid 4.6 billion yen (about $34.35 million) in gas bills, while it also paid about 5.4 billion yen (about 5.4 billion yen). $40.65 million) in revenue. In total, the Jared bot made a total of 254,000 transactions during this period, 98.31% of which were found to be related to the sandwich attack.
Over 60% of the Ethereum block was found to be occupied by Jared bot transactions in the week starting April 17, 2023. As a result, Ethereum gas prices have risen significantly, putting a strain on the network as a whole.
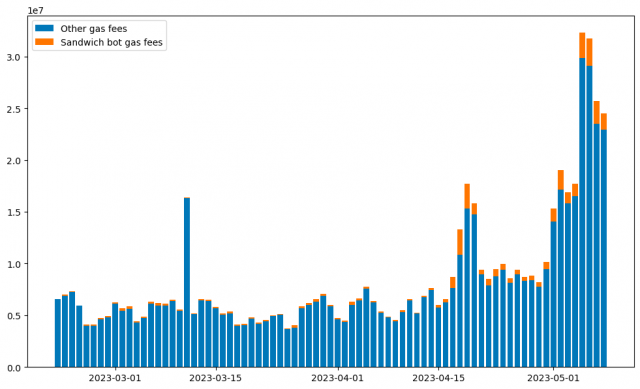
Source: Eigenphi
In early May 2023, Ethereum gas prices hit their highest level since May 2022. The average transaction cost rose dramatically from the lowest level of 9.07gwei in October 2010 to the highest level of 155.8gwei on May 5th. Average gas prices fell to 55gwei on May 13, but still remain high compared to previous levels.
connection:Ethereum transaction fees skyrocket, revealing involvement of Front-Rumbot
Sandwich attack countermeasures ①: DEX
DEX (Distributed Exchange) allows users to trade without going through a centralized exchange. Uniswap, SushiSwap, Balancer, Curve, etc. These platforms are sometimes targeted by sandwich attacks.
One measure available in DEX to prevent or mitigate sandwich attacks is the setting of a “slippage limit” or “tolerance”.
Slippage is the difference between the trade price predicted by the user and the price when the trade is actually executed. In other words, the slippage limit limits the risk of closing a trade at a price that deviates from the predicted price.
Most DEXs allow users to adjust their slippage tolerance. If the final trade price exceeds the slippage tolerance you set, the trade will be automatically canceled or returned.
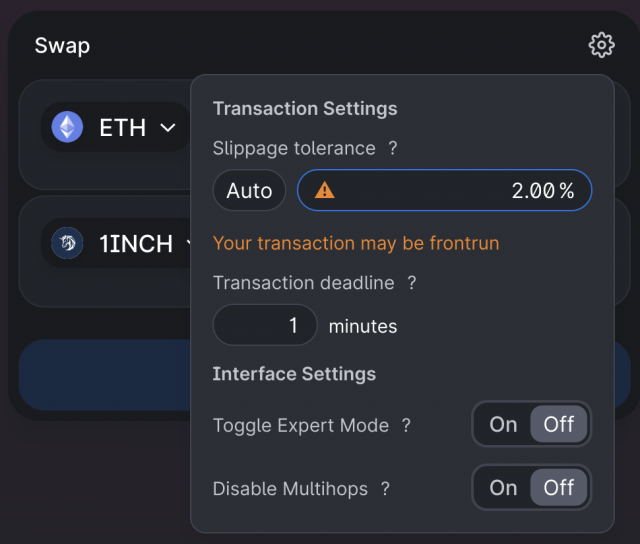
Source: Uniswap
For example, Uniswap allows you to freely change the slippage tolerance from the settings menu of the swap interface. This feature allows you to trade according to your own risk tolerance.
Additionally, another way to protect yourself from sandwich attacks is to use DEX aggregators. DEX aggregators scan multiple DEXs at once to source the best price and liquidity for orders to fulfill trades.
DEX aggregators also have the ability to reduce price impact and slippage by distributing large orders across multiple pools and routes. DEX aggregators that offer this type of service include 1inch, Matcha, Paraswap, and Slingshot.
By utilizing the above measures, it will be possible to make DEX transactions safer and more efficient.
Sandwich attack countermeasures ②: MEV Blocker
Sandwich attacks are a type of attack technique that exploits the order and timing of unconfirmed transactions.These attacks are carried out in a pool of waiting transactions called “mempool”. The profits generated by these attacks are collectively referred to as “MEV” (Miner Extractable Value).
To address this problem, a solution to prevent MEV, “MEV Blocker” was developed. According to MEV Blocker, more than ¥186 billion ($13.8 billion) has been extracted from MEV-related bots on Ethereum so far.
The role of MEV Blocker is to prevent MEV extraction while returning some to the user. Specifically, users can configure MEV Blocker as an RPC (Remote Procedure Call) to take advantage of private memory pools using unsigned transactions. Transactions collected here are processed by a group of users (searchers) who respond to MEV opportunities.
Source: MEV Blocker
Searchers are responsible for monitoring the flow of blockchain transactions and looking for potentially profitable opportunities (MEV). MEV Blocker provides an opportunity for searcher MEVs, but has certain rules in doing so. 90% of the MEV extracted by the searcher will be returned to the user of the original transaction, and the remaining 10% will be rewarded to the searcher.
This allows users to directly receive a portion of the value extracted from their own transactions. This is a mechanism to prevent users from unfairly losing profits due to front-running or other forms of MEV extraction.
MEV Blocker profit return scheme
MEV Blocker is a new initiative to protect users from MEVs such as sandwich attacks. It was jointly developed by organizations such as Balancer, ShapeShift, ParaSwap, etc., which provide the decentralized trading protocol “CoW Swap” and the decentralized relay “Agnostic Relayer” for validators.
MEV Blocker’s mission is to establish a fair trading environment by preventing unfair trading strategies such as front-running and sandwich attacks. To achieve this goal, MEV Blocker is designed with a focus on preventing front-running and sandwich attacks.
However, MEV Blocker only allows “backrun”. “Backrun” generally refers to the strategy of observing other people’s trades and then making a profit by making your own trades. It can be said that this is a kind of act of “stealing delicious things”. Searchers are leveraging the information they gain with MEV Blocker to allow them to profit from backruns and return most of it to the user who initiated the transaction.
In other words, MEV Blocker is designed to strike a balance between preventing frontrunning and sandwich attacks while returning some of the MEV to the user through backrunning. This initiative aims to improve the fairness of blockchain transactions, and aims to create an environment where users can trade with peace of mind.
If a system like MEV Blocker is widely used, it is possible that MEV retrieval by front-running and sandwich attacks will be suppressed, and the ratio of MEV retrieval by back-running will increase.
– 1 Million transaction, all protected from frontrunning
– 1500 refunds paying out >130 ETH
– currently >5% of all Ethereum tx using itReally happy that with MEVBlocker we have been able to make a significant shift in the MEV game in favor of the user.
— Martin Köppelmann (@koeppelmann) May 23, 2023
Released on April 5, MEVBlocker will protect more than 1 million transactions from front-running by May 24, according to Martin Köppelmann, co-founder of Gnosis and CowSwap, who was involved in the creation of MEV Blocker. said he did. MEVBlocker currently processes over 5% of all Ethereum transactions and has paid out over 130 ETH in refunds to date, minimizing the impact on users.
Discussion of MEV Burn
MEV Blocker presents a way to coordinate the incentives of various participants in the network, such as validators and searchers, to acquire MEV (Miner Extractable Value). In the past, MEVs were seen as an example of system inefficiency. However, MEV Blocker explores new ways to redistribute more MEVs to users.
This idea has many implications, such as minimizing MEVs, returning them to users, and even incinerating excess MEVs (removing them from supply).
Among them, “MEV Burn” is attracting particular attention. This is a method similar to EIP-1559, and the concept is to introduce a mechanism to incinerate a part of MEV and increase the value of ETH (Ethereum) as a result. Specifically, the right to generate a block is auctioned at the consensus layer of the blockchain, and the person who proposes to burn the most ETH wins the right.
What is EIP-1559
EIP-1559 is a proposal to improve the gas fee system in Ethereum’s major update “London” in August 2021. By making changes such as “Abolishing the first price auction method of Ethereum and introducing a fixed price selling mechanism”, “Doubling the block capacity and changing the system to change the capacity according to the transaction volume”, the congestion of the network will be relieved, We plan to reduce gas costs.
 Cryptocurrency Glossary
Cryptocurrency Glossary
It is based on the concept that the rights to create blocks are auctioned at the consensus layer of the blockchain, and whoever proposes to burn the most ETH wins.
There are two main effects of MEV Burn.
The first is “MEV smoothing”. This is to ensure overall MEV security by reducing the variability in the MEV that each validator gets and making the distribution of rewards as even as possible.
The second is “MEV redistribution”. The idea is to improve the macroeconomics of the entire system by distributing MEV to users rather than validators.
Through these efforts, the perspective on the treatment of MEVs is gradually changing. And this new system could also have macroeconomic benefits for users. This is because the burning of ETH reduces the supply, which may increase the value of ETH. In addition, there is the potential to reduce transaction costs as users no longer have to pay excessive security costs.
The idea of MEV Burn is being discussed by Ethereum Foundation researcher Justin Drake and bloXroute Labs CEO Uri Klarman. Since no definitive method has yet been found for handling MEVs, attention is focused on future research and development.
Commentary on Sandwich Attacks and MEV, Threats to Decentralized Trading Markets and Countermeasures Our Bitcoin News.








